On March 3, 2016 the Kalachnikov E-security team launched its official channel on the encrypted messaging app Telegram. According to the Kalachnikov E-security team, its aim is "to publish various web-hacking techniques, exploits, [and] articles with... information and [the] latest cyber attacks." On March 6, 2016, another Telegram channel was launched under the name Kalachnikov Team. Both channels are primarily in English and target a Western audience. However, both channels frequently cite "Mosul time," indicating possible geographic ties with the Iraqi city, which is under ISIS control.
Although related, the Kalachnikov E-security team channel places greater emphasis on technical support to jihadi cyber activists, while the Kalachnikov Team channel acts as a mouthpiece, uploading ISIS-related jihadi literature, sharing posts from cyber jihadi groups, and reporting successful attacks on websites and Facebook pages. Furthermore, the Kalachnikov Team channel maintains an active Facebook page and WordPress site highlighting the group's activities. As of April 1, 2016 the Facebook group has received 27,777 likes. It is worth noting that the Kalachnikov Team Facebook page was last active in September 2014, while its most recent WordPress activity is from November 2013. Meanwhile, both Telegram accounts remain active, indicating a shift in the usage of social media platforms by ISIS-related jihadi organizations. The separation of Kalachnikov's technical and propaganda activities underscores its aim to boost cyber jihadi enthusiasm while providing technical education to current and potential team members.
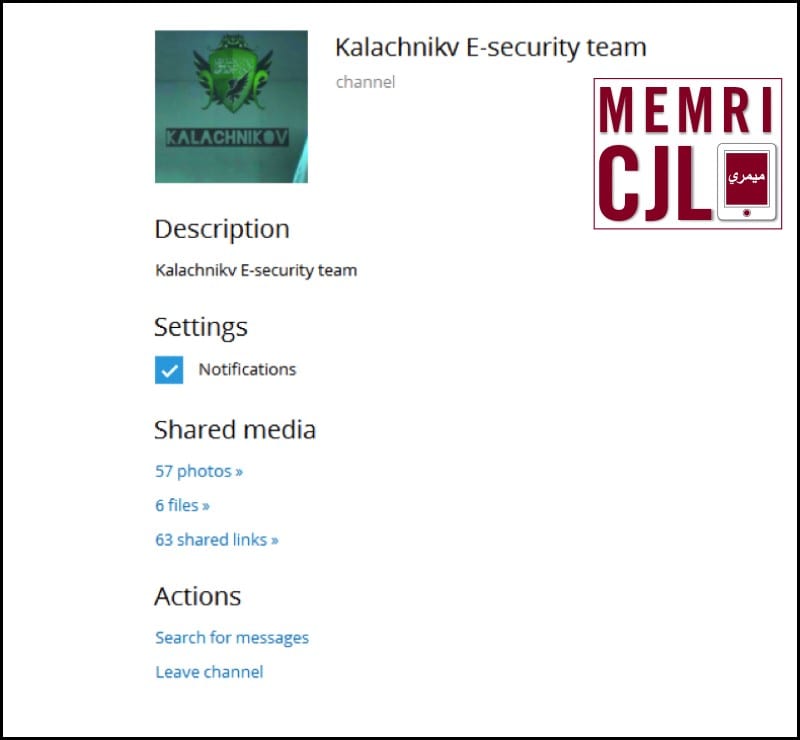
 Kalachnikov's two Telegram channels
Kalachnikov's two Telegram channels
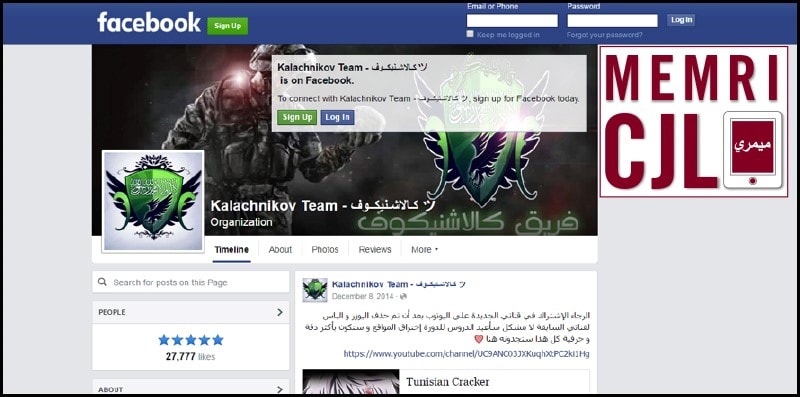 Kalchnikov Team's Facebook page on April 1, 2016
Kalchnikov Team's Facebook page on April 1, 2016
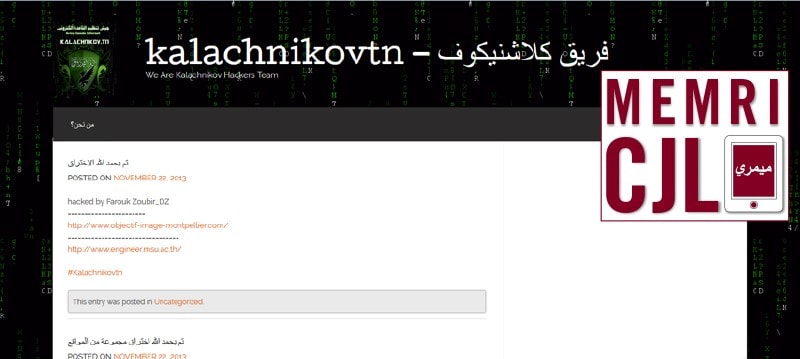 Kalchnikov Team's WordPress site on April 1, 2016
Kalchnikov Team's WordPress site on April 1, 2016
 Kalachnikov's logo
Kalachnikov's logo
One of Kalachnikov Team's first posts on March 6, 2016 referred to the Kalachnikov E-Security team, noting the two shared a "single goal of [advocating] electronic jihad" while hoping for cooperation between them. The post was written by "Ayyoub Al-Maghribi" ("the Moroccan").
On March 3, 2016, the Kalachnikov E-security team shared a link to the Virtual Private Network (VPN) software VPNGate. VPN software is used to encrypt an online connection. The utilization of VPN for communication, uploading, and downloading increases network security and makes it harder to trace the connection.
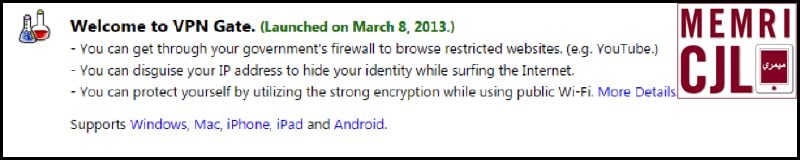 VPNGate highlights the functions of its software.
VPNGate highlights the functions of its software.
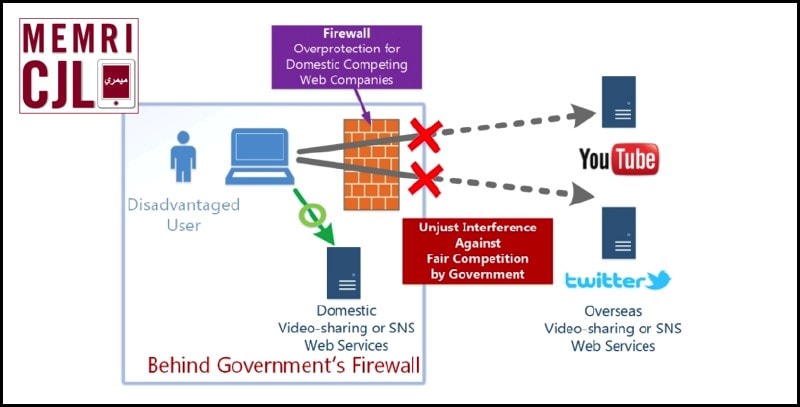 VPNGate displays the perceived effects of government's firewall.
VPNGate displays the perceived effects of government's firewall.
Kalachnikov E-security team mocked Anonymous hacktivists for blocking its Twitter account on March 4, 2016 as part of Anonymous's campaign against ISIS digital media, which was launched in in November 2015. Groups supporting ISIS use advanced online software to circumvent both government and hacktivist efforts to shut down their accounts.

On March 4, 2016, Kalachnikov E-security team boasted of an attack on an Italian web server, claiming it had gained "full access." It also provided a description of what a web server is for the potential hacker.
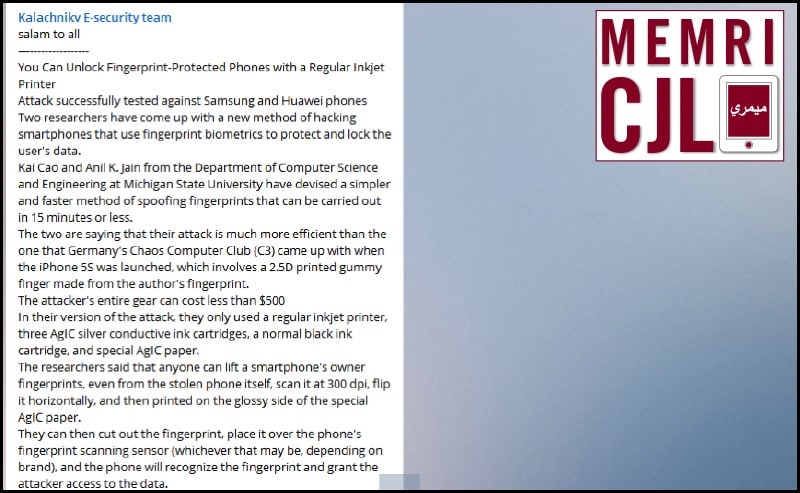
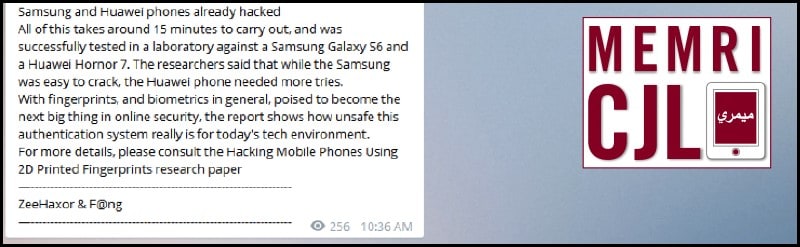
Kalachnikov E-security team posted about successful attempts at hacking fingerprint-protected Samsung and Huawei phones. According to the group, the process takes approximately fifteen minutes and with hacking gear costing less than $500.
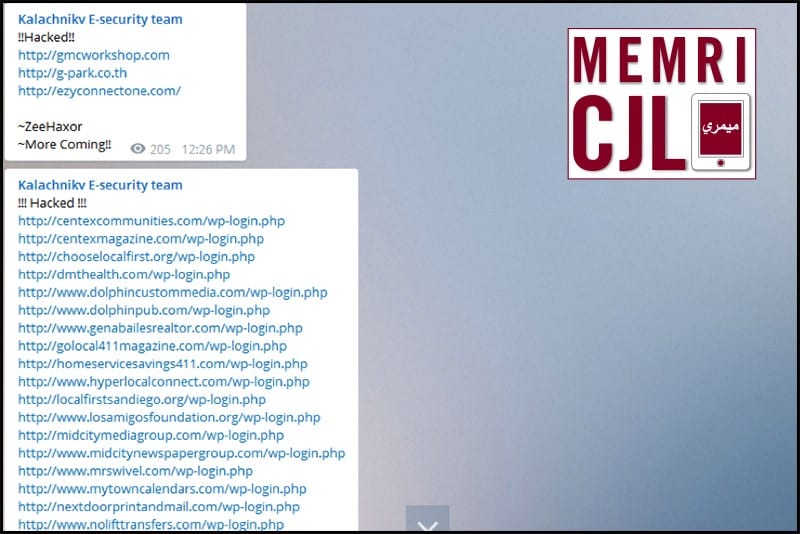
On March 8, 2016 Kalachnikov E-security team posted a list of websites it had allegedly hacked. A number of the websites that have been hacked are no longer online. Additionally, the majority of sites appear to be Western.
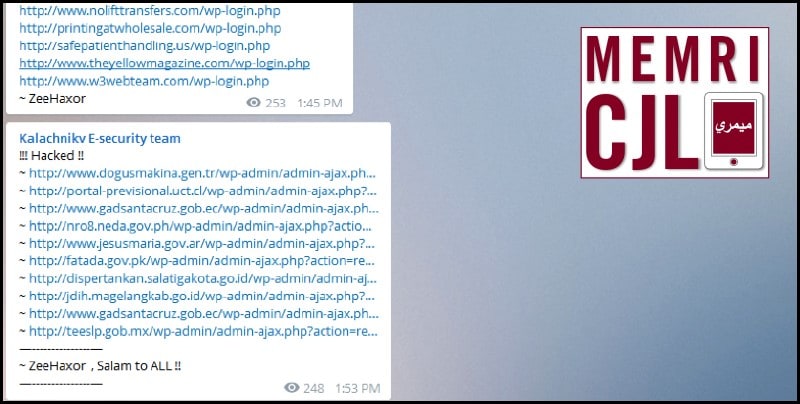
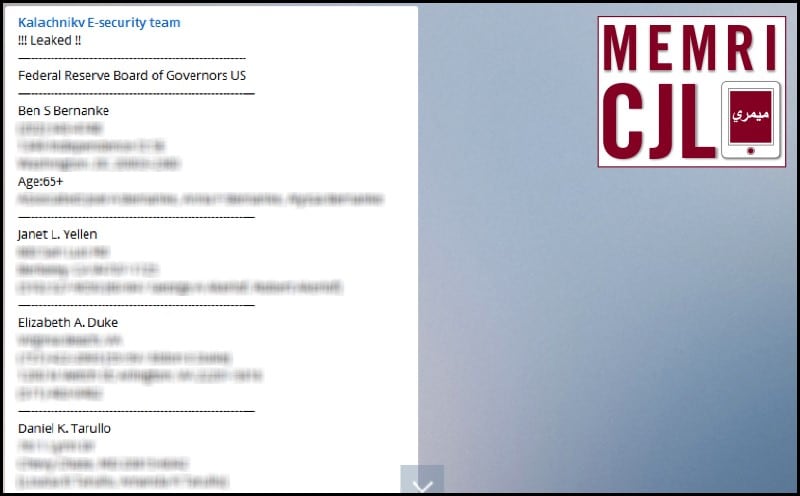
On March 9, 2016 the Kalachnikov E-security team published the supposed addresses of current and former members of the United States Federal Reserve Board of Governors, including Ben Bernanke and Janet Yellen. (Note: Personal info redacted by MEMRI)

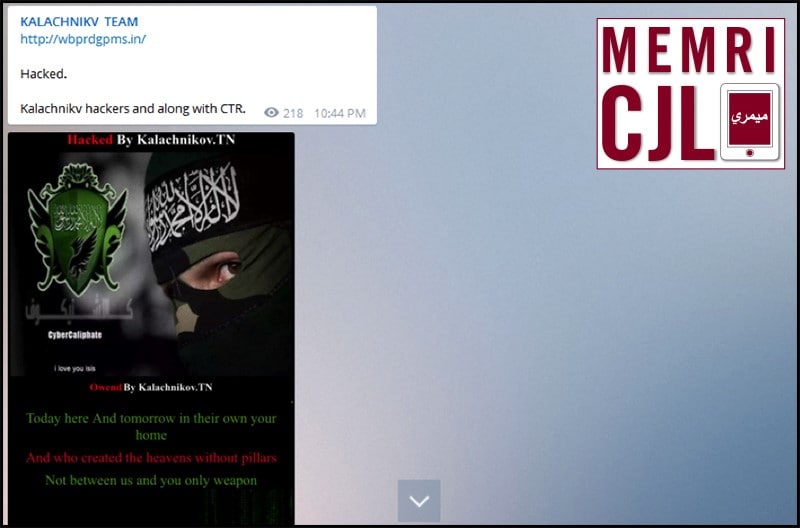
On March 9, 2016 Kalachnikov Team claimed to have conducted a joint hack with Cyber TeamRox (CTR), a related online jihadi organization.[1]
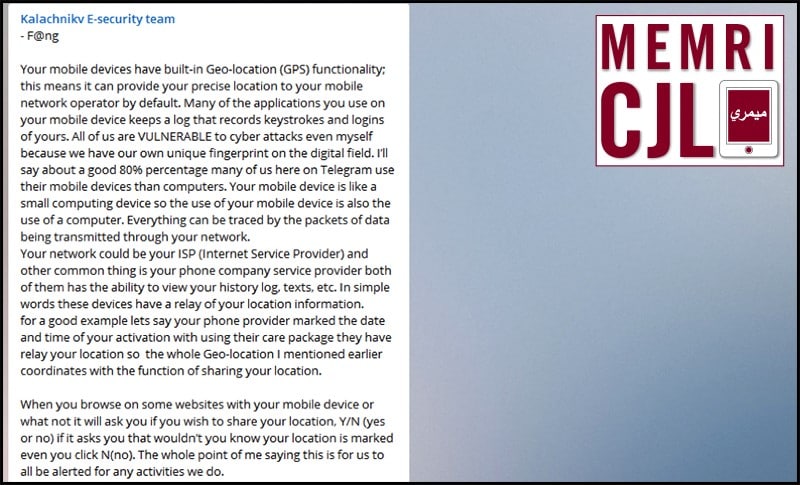
On March 17, 2016 Kalachnikov E-security team highlighted the risk of followers being located while using electronic devices and related services. According to Kalachnikov E-security team, this is done by the use of the GPS chips in mobile phones, as well as by mobile application data logs, Internet Service Provider (ISP) data logs, and mobile service provider data recording. Regarding the use of mobile devices, the group warns that "everything can be traced by the packets of data being transmitted through your network." Kalachnikov E-security team also warns followers using mobile devices that "some websites," regardless of whether the user decides to consent to geolocating services or not, have locating capabilities. That said, Kalachnikov E-security team advises followers to use prepaid phones as a method to mitigate the aforementioned concerns.
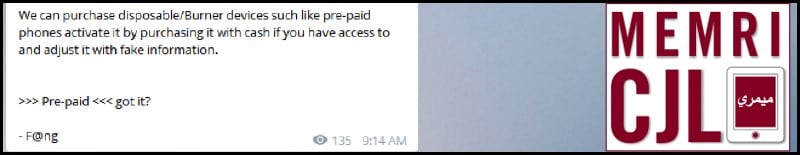 Kalachnikov instructs users to use disposable/burner devices paid for in cash as a method of surveillance circumvention
Kalachnikov instructs users to use disposable/burner devices paid for in cash as a method of surveillance circumvention
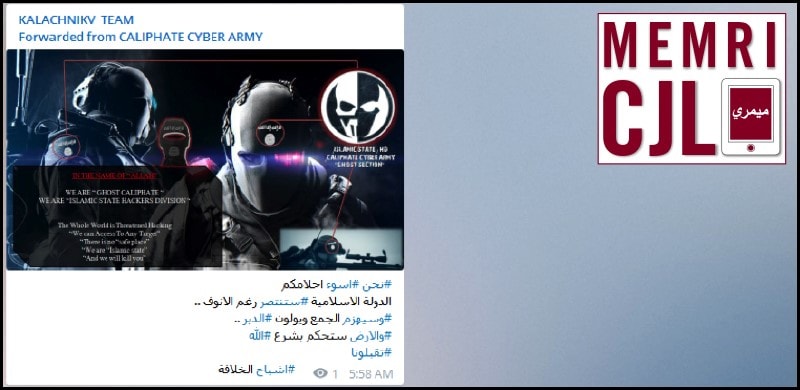
Kalachnikov Team forwarded a Cyber Caliphate Army post which claimed to be the "Islamic State Hackers Division" on March 13, 2016.
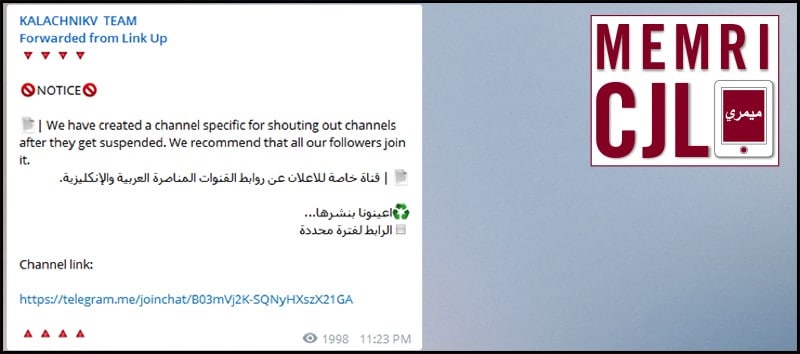
On March 15, 2016 Kalachnikov Team forwarded a post by the group Link Up, which discussed a channel for "shouting out channels after they get suspended." As cyber jihadi organizations experience channel shutdowns, new channels quickly emerge.
On March 19, 2016 Kalachnikov advertised the pro-ISIS Telegram channel Dabiq, which is named after ISIS's English-language magazine of the same name.

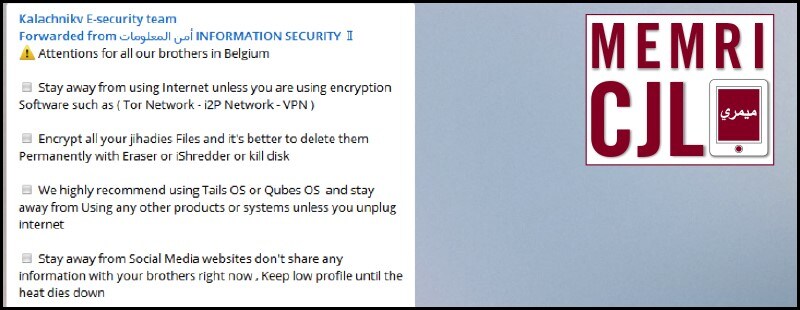
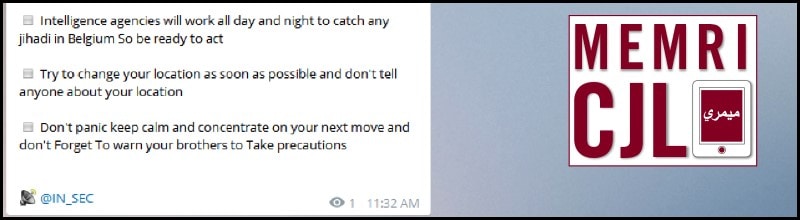
Following the March 22, 2016 ISIS attacks in Brussels, Kalachnikov E-security team forwarded security measures directed to "brothers in Belgium." The post included various methods of avoiding physical and online surveillance including avoiding social media, encryption, recommended Operating Systems, and physical location change.[2]
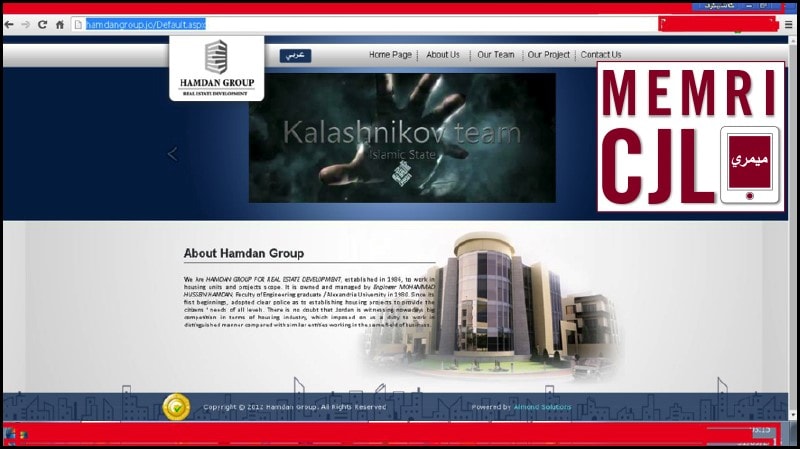
March 30, 2016, Kalashnikov team advertised the hacking of the Jordanian real estate company Hamdan Group.
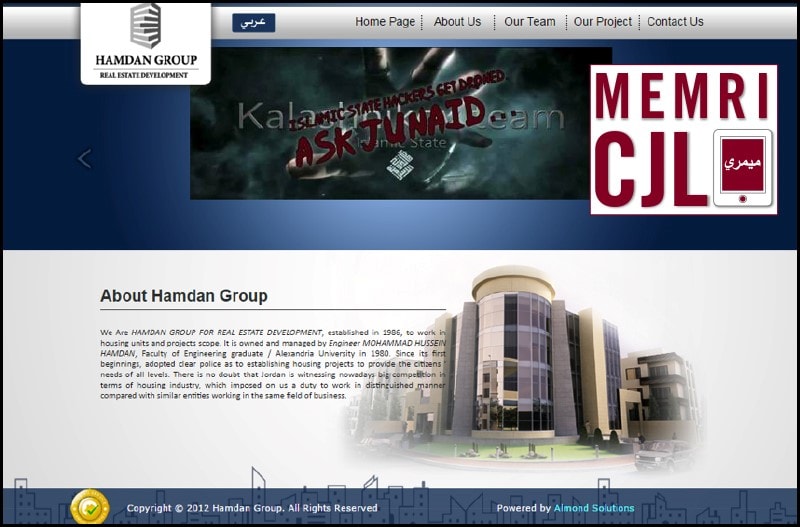
Following the Kalashnikov team hack of Hamdan Group, an apparently rival hacking organization taunted Kalishnakov Team by altering its work and commenting that "Islamic State Hackers Get Droned - Ask Junaid. [3]"
Endnotes:[1] See MEMRI CJL Report, Jihadi Hacking Group Cyber TeamRox (CTR) Active On Telegram, Facebook, March 9, 2016.
[2] See MEMRI CJL Report, Pro-ISIS Hacking Group Posts Security Instructions Following Brussels Attacks, March 22, 2016.
[3] A reference to leading ISIS hacker Junaid Hussain, who was killed in a drone strike in Al-Raqqa in August 2015.Latest Posts