The following report is a complimentary offering from MEMRI's Jihad and Terrorism Threat Monitor (JTTM). For JTTM subscription information, click here.
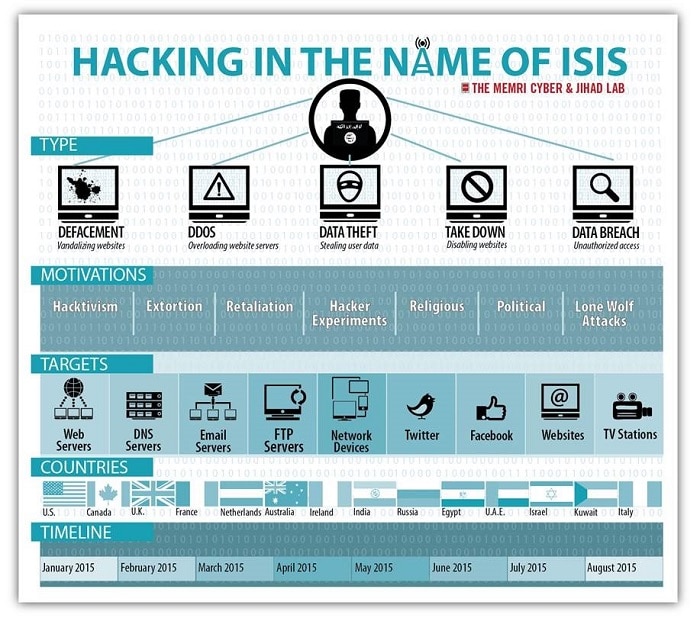
Table Of Contents Introduction I. Table: Hacks By ISIS And Pro-ISIS Elements: A Chronology II. ISIS Hacking Activity III. Hacking Activity By ISIS Supporters And Pro-ISIS Hacker Groups IV. The Islamic State Hacking Division (ISHD) V. The CyberCaliphate VI. ISIS Cyber Operations And Counter Operations IntroductionOver the past year, Islamic State (ISIS) and pro-ISIS hackers, as well as hackers claiming to be associated with or operating in the name of ISIS, have been conducting cyber attacks throughout the world. The targets have included media outlets, government agencies, universities, NGOs, and businesses, from the very large to the very small.
Latest Posts