Table Of Contents
From Al-Qaeda To The Islamic State, Jihadi Groups Engage In Cyber Jihad - An Introduction By Ambassador R. James Woolsey, Former CIA Director And MEMRI Board Of Advisors Member
- Early Jihadi Online Activity: Google Blogs, Yahoo-Hosted Websites
- Shumoukh Al-Islam, Al-Fida' and AMEF - Al-Qaeda's Online Open University
- The First Cyber Jihad Groups Emerge
- On Al-Qaeda-Affiliated Websites And Forums: Cyber Jihad Training, Claims Of Cyber Attacks Against U.S. Airports, Government Agencies Including FBI, CIA, Open Source Center, And The White House, As Well As Military Bases
- October 2006: Mujahideen Gather Information on Anchorage International Airport
- 2006-2007: Islamist Hackers Focus On U.S. Government: Military, FBI, CIA
- 2009-14: Hacking And Using Drones
- February 2010: Online Jihadis Discuss Cyber Targets in U.S. - Including Government Buildings Like White House, CIA HQ
- January 24, 2011: Jihadis Plan Cyber Attack on U.S. Government Computers
- June 2011: Shumoukh Al-Islam Writer Calls For Establishing 'Center For Electronic Terrorism' - Which Is Now In "Initial Testing Lab Phase" Prior To Targeting The U.S.
- March 2013: Al-Qaeda Electronic Army And Tunisian Cyber Army Claim To Have Hacked Pentagon, State Department Websites
- March 2013: Al-Qaeda Claims To Have Hacked U.S. Government's Open Source Center
- April 2013: Using Android Smartphones To Hijack Airplane
- May 2013: Ansar Al-Mujahideen Forum Discusses 'Anonymous' Cyber Attack That Paralyzed Guantanamo's Wi-Fi
- September 2014: ISIS-Supporter "Jihadi Media Platform" Forum Posts Instructions For Disrupting And Downing Drones Used By U.S. In Iraq
- Al-Qaeda's Embrace of Encryption Technology 2007-2014
III. Statements By Al-Qaeda Leadership On The Importance Of Cyber Jihad
- Osama bin Laden: "The Wide-Scale Spread Of Jihadist Ideology, Especially On The Internet... [Is] A Major Achievement For Jihad"
- Ayman Al-Zawahiri On Cyber Jihad: "A Great Front of Islam"
- Adam Gadahn, American Al-Qaeda Spokesman - And Jihadi Media And Cyber Pioneer
- Islamic State Of Iraq's Minister Of War: "We Believe Electronic Warfare Is [The] War Of The Future"
- Senior Al-Qaeda Commander to Potential Recruits: We Need "Specialist Cadres," Not "Regular Fighters" In Afghanistan-Pakistan
- AQIM Publishes First Installment In Electronic Jihad Series
- Jihadis Discuss Reported Breach Of TOR, Complain That Tech-Savvy Forum Members Have Abandoned Forums For Twitter
- AQAP Commander Calls On Followers To Learn Tools for Cyber Jihad From The Internet
- AQAP Deputy: Online Jihad Is A Great Front And Part Of The Coming Phase
- AQAP Deputy Leader and Former Osama bin Laden Secretary Nasir Al-Wuheishi Calls For Volunteers to Join Al-Qaeda Via Encryption Software
- Anwar Al-Awlaki - The "Bin Laden Of The Internet": The Internet Is A Great Medium For Spreading Jihad
- Inspire Editor Samir Khan Warns The West That Al-Qaeda Cyber Activists Are Studying Internet Security, Praises The Impact Of Made-In-Afghanistan Jihadi Videos That Are Distributed In The Streets Of London And California
- U.S.-Designated Global Terrorist Abu Adam Al-Almani: Al-Qaeda's "Professional Media Work" In German And English "Reached Us In Germany"
IV. A Major Shift In Online Jihad: From Forums To Social Media
- Following Killing Of Al-Awlaki and Khan, Al-Qaeda Cyber Activists Promise To Spread Online Jihad And Raid Facebook And Twitter
- American Al-Qaeda Spokesman Adam Gadahn: "We Must Make Every Effort To Reach Out To Muslims Through New Media Like Facebook and Twitter"
- Bali Bombing Mastermind: "This Is The Internet Era, There Is Facebook, Twitter, And Others"
- Taliban Spokesman Praises Impact Of Online Jihad And Use Of Facebook And Twitter
- Jihadi News Agency "Kavkaz Center," Affiliated With Designated Terrorist Organization "Caucasus Emirate," Calls For Followers To Use Twitter and Facebook
- Former Guantanamo Detainee And Al-Qaeda Cyber Activist Praises Online Jihad: "Especially Through Twitter And Facebook"
- U.S.-Based Social Media Companies - The Engine Of Jihad Today
- The San Francisco-Based Internet Archive - Platform For Uploading And Downloading Al-Qaeda Content: Fast, Free, And Unobstructed For Terror Organizations
- YouTube - The Internet's Primary and Rapidly Expanding Jihadi Base
- Twitter - Hashtag Jihad And Fundraising For Jihad
- Friending Al-Qaeda On Facebook
- Designated Terrorists And Terrorist Organizations Online: Maintaining Official Websites, Using Google Blogspot, Using Yahoo Server, Launching Internet Radio Stations
VI. Social Media In The Syria And Iraq Conflict
- Calls To Engineers To Join The Islamic State - By IS Caliph Al-Baghdadi And Others, Including Foreign Jihadis
- Jihadi Hacktivist Groups Emerge In ISIS
- Death Photos, Eulogies For Jihadis Killed In Battle Used As A Recruitment Tool
- Skype - Fundraising And Media Interviews
- Whatsapp - Mobile Jihadi Messaging
- Google Services - Mapping, Blogging, And Apps
- Instagram - Sharing Photos Of Al-Qaeda Leaders - And Used By Jihadis In Syria And Iraq
- Flickr - Snapshots Of Martyrdom
- Tumblr - Microblogging Jihad
- Ask.fm - Jihadi Q&A; Kik - More Privacy
- SoundCloud - Jihadi Recordings
- ISIS's Extensive Use Of Social Media
- Friendica and Diaspora
- VK.com
- Justpaste.it
- Algorithms: Helping Jihadis Find Each Other - Even After Social Media Accounts Are Shut Down
VII. The Future of Online Jihad - The Coming Battle With The Cyber Army Of Al-Qaeda And Its Offshoots VIII: Endnotes
An Introduction By Ambassador R. James Woolsey, Former CIA Director And MEMRI Board Of Advisors Member
One of the most important challenges facing the United States and the Western world is that of cybersecurity, and understanding the intentions and capabilities of jihadi groups in this realm. It therefore gives me great satisfaction to introduce an historic study that the Middle East Media Research Institute's (MEMRI) Jihad and Terrorism Threat Monitor (JTTM) has been working on for the past year. Given the current situation of Western recruitment to jihad in Iraq and Syria, the information in this study could not be timelier.
One can hardly imagine the development of the global jihad movement to its present proportions without the Internet - and at the heart of the jihadi organizations' strategy are U.S. social media companies. Over the past few weeks, senior government officials, including the heads of the FBI and CIA have been discussing the Islamic State's (ISIS) and other jihadi groups' dependence on social media. Last month, FBI director James Comey said that the Islamic State's "widespread use of media and growing online support intensified following the commencement of U.S. airstrikes in Iraq." In addition, the 9/11 Commission Review report noted in July that "cyber attacks can constitute another form of asymmetric terrorism. Security officials are concerned that terrorist groups' skills in computer technology - and in particular in manipulating offensive cyber capabilities - will increase in the years ahead..."
This following report documents jihadi use of the Internet, from Al-Qaeda's and other groups' earliest websites and forums in the 1980s to what we see today with the Islamic State: highly professional video productions and widespread presence on social media, which are integral for recruiting and training the next generation of jihadists.
The study will be a vital contribution to understanding this phenomenon, and even more importantly in discussing possible ways of countering it; it also could not be timelier, as it is being released to coincide with the launch of MEMRI's latest initiative, the Cyber and Jihad Lab (CJL). This initiative monitors, tracks, translates, and researches cyber jihad originating from the Middle East, Iran, South Asia, and North and West Africa. It translates information from Arabic, Farsi, Urdu, Pashtu, Dari, and other languages into English, produces detailed analyses, and innovates and experiments with potential solutions for stopping cyber jihad. It too will be an important contribution to the effort.
What you are about to read chronicles Al-Qaeda's earliest cyber activity; the emergence of the main Al-Qaeda websites and forums and their development into providers of training for hacking, spreading viruses, and other forms of cyber attacks; statements by Al-Qaeda leadership on the importance of cyber jihad; and the major shift in online jihad from jihadi forums to Western social media, which is now depended upon by jihadis for outreach efforts in the current Syrian and Iraqi conflicts. It explores how nearly a decade has now passed since the U.S. government first pledged to deny terrorists use of the Internet, whereas jihadi activity in cyberspace seems to grow daily. This generation's activists of Al-Qaeda and its offshoots, led by the Islamic State, are younger and Internet savvy, having heeded previous Al-Qaeda leaders' calls to turn to the Internet. They are connected via Facebook, Twitter, YouTube, Instagram, Flickr, and every other emerging social media platform, adopting them almost as soon as they are created - just like the younger generation in the West. Like their Western counterparts, they have smartphones, tablets, and other devices; and, like everyone else, they purchase and use apps.
It is important to note that with the combination of social media and mobile devices, jihadi outlets can make sure that their content is viewable anywhere, anytime. Jihadis were quick to use YouTube and other video sharing services, taking advantage of this technology to provide courses and training in explosives manufacture, weapons training, and hacking. Today, anyone can receive tweets or Facebook posts from Al-Qaeda and its offshoots, led by ISIS, and other terrorist groups, directly to their cellphones, in real time - and can immediately share them far and wide. Another aspect of cyber jihad is hacking; jihadis and jihadi groups are already obtaining funds and wreaking havoc by hacking financial institutions and individuals. This will continue to become more widespread in the future.
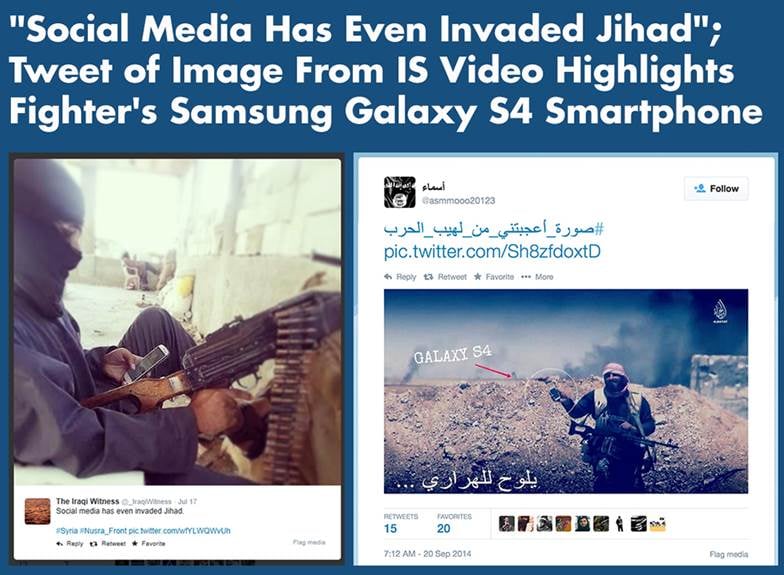
In the photos that they now disseminate on social media, the jihadis, who used to pose in their traditional garb surrounded by weapons such as assault rifles and grenades, nowadays include in these photo images a laptop, smartphone, and tablet, reflecting the importance placed on these "weapons." Fittingly, these photos are often chosen as the profile images for their social media accounts.
This landmark study sheds light on a hugely important area that Western governments, militaries, and academics know too little about. It should be read by everyone in Washington - from the Department of Homeland Security and legislators on Capitol Hill to the Pentagon cyber force, and those in academia studying the cyber realm.
*Ambassador R. James Woolsey is a former director of the CIA, former under-secretary of the Navy, and former Ambassador to the Negotiation on Conventional Armed Forces in Europe (CFE). He is also a member of MEMRI's Board of Advisors.
Over the past 20 years, Al-Qaeda and other jihadi groups have been quietly investing in their cyber jihad capabilities. As Abu Ubayd Al-Qurashi, one of Osama bin Laden's closest aides, warned the U.S. in 2002, "jihad on the Internet" has now become one of the "nightmares" to be faced in the future.[1] Al-Qaeda news and information, once conveyed to followers via messengers, fax, and the Qatari television network Al-Jazeera, is now promoted by a new, Internet-savvy generation of jihadis. From their very earliest ventures into this sphere that included jihadi websites, forums, and discussion groups, whose members were carefully screened, they have moved onto today's social media platforms. They use these platforms not only to spread their messages, but, as this report will show, to recruit activists with computer and Internet skills who are actively involved in studying how to hack the websites of government institutions and banks, hijack drones and aircraft, and carry out other cyber crimes.
With the latest transition by Al-Qaeda and its offshoots, including ISIS, to social media, all of this content is now accessible to the entire world. Anyone, from journalists to the general public, can now follow, "like," "friend," re-tweet, submit questions to, view photos posted by, and conduct dialogue with Al-Qaeda and other jihadi groups online - and can just as easily be recruited by it. The advent of social media has changed the status quo; while Al-Qaeda and the main jihadi media groups have lost a great deal of their control over their own public relations efforts, they are now reaching a much larger - and constantly growing - pool of potential recruits.

The previous main jihadi forums were always private, with their own internal hierarchy; there was an online application process for anyone requesting to join and they also had to be vouched for by trusted forum members. Thus, the circle of online jihadis was limited. From these closed forums, the online jihad of Al-Qaeda and its offshoots expanded to countless websites and other, less important forums and blogs that were open and that primarily reposted and redistributed content. Jihadi media groups were established, and the new content that they provided included increasingly professional video productions and online magazines, including in English as well as in European languages.
Since the launch two decades ago of what is considered one of the "first real Al-Qaeda website[s],"[2] Azzam.com, whose operators pleaded guilty to terrorism charges in December 2013 in a U.S. federal court, the importance of cyber jihad has been discussed by the Al-Qaeda leadership. This includes Osama bin Laden and Ayman Al-Zawahiri as well as the heads of Al-Qaeda's offshoots Al-Qaeda in the Arabian Peninsula (AQAP), Islamic State of Iraq (ISI), the Somali Al-Qaeda affiliate Al-Shabaab Al-Mujahideen, and Al-Qaeda in the Islamic Maghreb (AQIM), as well as by the leadership of other jihadi groups such as the Taliban, and, now, the Islamic State (previously known as the Islamic State in Iraq and Syria, or ISIS) and others.
'Abd Al-Bari 'Atwan, the pro-jihad author and former editor of the London daily Al-Quds Al-Arabi, who in 1996 interviewed Osama bin Laden and is known to be close to Al-Qaeda, wrote in a chapter titled "Cyber Jihad" in his 2008 book The Secret History of Al-Qaeda that by the mid-1980s, Sheikh Abdullah Azzam, the Palestinian Sunni Islamist cleric and Osama bin Laden mentor who convinced bin Laden to come to Afghanistan to aid the jihad, was "encouraging jihadi groups to exploit the potential of evolving electronic technologies." 'Atwan added: "The Internet has become a key element in Al-Qaeda training, planning, and logistics, and cyberspace a legitimate field of battle. Some commentators have gone so far as to declare that Al-Qaeda is the first Web-directed guerrilla network."[3]
Pakistani journalist and bin Laden biographer Hamid Mir, who in the summer of 2014 was attacked by gunmen in Karachi, noted, as he watched Al-Qaeda members fleeing a U.S. bombardment of their training camps in November 2001: "Every second Al-Qaeda member [was] carrying a laptop computer along with his Kalashnikov."[4]
One early Al-Qaeda recruit, the Moroccan L'Houissaine Kherchtou, was sent by the Al-Qaeda leadership to learn high-tech methods of surveillance from Abu Mohamed Al-Amriki ("The American"), the Egyptian-born American who was a key aide to bin Laden.[5] Kherchtou and other trainees learned about potential targets such as bridges, major sports stadiums, police stations, and consulates. He then joined Al-Qaeda's electronic workshop at Hyatabad in Peshawar, Pakistan, according to his February 21, 2001 testimony in United States of America v. Usama bin Laden, et al.[6]
Another early figure in Al-Qaeda cyber activity was Irhabi 007, aka Younes Tsouli, a 23-year-old Moroccan-born resident of the U.K. In 2007, he was found guilty of incitement to commit acts of terrorism, and sentenced to 16 years in a U.K. prison. Tsouli, considered the godfather of online jihadis, was contacted by Al-Qaeda in Iraq leader Abu Mus'ab Al-Zarqawi and promoted and spread Al-Qaeda online.[7]
The "sacred duty" of cyber jihad was codified by Al-Qaeda in a 2003 Al-Qaeda document called "The 39 Principles of Jihad," on the Al-Farouq website, a known Saudi-based Al-Qaeda domain. This duty includes participation in online forums to defend Islam. "Al-Salem," who posted the document, noted that the Internet offers a way of reaching millions of people in seconds, and that those with Internet skills are encouraged to use them to support the jihad by hacking "enemy" websites as well as "morally corrupt" ones such as pornographic sites.[8] Years later, Bostonians Ahmad Abousamra, who is on the FBI's Most Wanted Terrorists list and is thought to be currently in Syria helping ISIS,[9] and Tarek Mehanna, who is serving 17 years in federal prison after being found guilty of translating material for Al-Qaeda in Iraq, were found to have translated the "39 Principles" into English and posted it on a list serve called At-Tibyan Publications, where English-speaking Muslims praised Al-Qaeda.[10]
Defense, intelligence, security, and military authorities are becoming increasingly aware of the issue of terrorists' use of the internet as part of cyber security. For example, at a January 29, 2014 U.S. Senate Select Committee on Intelligence hearing, Defense Intelligence Agency director Lt.-Gen. Michael Flynn added: "I think that what is a serious threat that we are paying very close attention to are these non-nation-state groups and actors, Al-Qaeda being among them... that are also operating in the cyber domain... [T]hey are increasingly adapting to an environment that is actually benefiting them." He added that this is "an increasingly growing threat." But, as this report shows, such online activity has been developing over the past two decades.
John Carlin, the Assistant Attorney General for National Security in the U.S. Department of Justice, said on July 24, 2014 at the Aspen Security Forum session titled "U.S. Counterterrorism Strategy and its Implications for Emerging National Security Threats": "[L]ooking ahead on cyber terrorism - and the 9/11 report just gave an updated report - we're in a ... pre-9/11 moment with cyber. It's clear that the terrorists want to use cyber-enabled means to cause the maximum amount of destruction as they can to our infrastructure. It's clear because they have said it. [Al-Qaeda leader] Zawahiri put out a videotape statement saying, 'We want to commit a cyber attack against the United States.' It's also clear that other actors - nation-state actors... have the capability now to cause significant damage." The 9/11 Commission's report to which Carlin was referring, released July 22, 2014 and titled "Reflections on the Tenth Anniversary of The 9/11 Commission Report,"warned: "Cyber attacks can constitute another form of asymmetric terrorism. Security officials are concerned that terrorist groups' skills in computer technology - and in particular in manipulating offensive cyber capabilities - will increase in the years ahead..."
At the heart of jihadi operations today in Syria and Iraq, and other places, are Western social media companies; cyber space is now part of their arsenal and will only become more central to them in the future.
As Robert Hannigan, newly appointed director of Britain's Government Communications Headquarters (GCHQ), which works closely with MI5, MI6, and the U.S.'s NSA, wrote in the Financial Times on November 3, 2014, "the largest U.S. technology companies which dominate the web": "However much they may dislike it, they have become the command-and-control networks of choice for terrorists and criminals, who find their services as transformational as the rest of us. If they are to meet this challenge, it means coming up with better arrangements for facilitating lawful investigation by security and law enforcement agencies than we have now... [W]e need a new deal between democratic governments and the technology companies in the area of protecting our citizens."
To highlight how important the cyber realm is to them, jihadis, who in previous years commonly posed for photos wearing their traditional garb and surrounded by weapons such as assault rifles and grenades, today pose similarly but with a laptop, smartphone, and tablet added to their arsenal; they frequently choose these images as profile images for their social media accounts.
This report will summarize the development of Al-Qaeda's and its affilate groups' cyber efforts, from the earliest closed online jihad websites and forums to its transition into social media accessible to all.
Latest Posts





