Introduction
The current fight between the U.S. government and Apple, in which the FBI is seeking Apple's assistance in unlocking the phone of San Bernardino shooter Syed Rizwan Farook,[1] is just the most recent example highlighting jihadis' use of Apple devices and products. Among jihadi groups affiliated with the Islamic State (ISIS), Al-Qaeda, and other organizations, and their followers and sympathizers, Apple products - including iPhones - are widely popular, and the best ways of utilizing them is a topic of jihadi discussions.
 German rapper-turned-ISIS-member Denis Cuspert aka Deso Dogg aka Abu Talha Al-Almani, and his Apple laptop. He was killed in a U.S. drone strike in October 2015.
German rapper-turned-ISIS-member Denis Cuspert aka Deso Dogg aka Abu Talha Al-Almani, and his Apple laptop. He was killed in a U.S. drone strike in October 2015.
Regardless of the outcome of the current Apple vs FBI fight over cracking the encryption of a single iPhone, it is important to realize that this is just one of a number of issues involving cyber jihad that concern both the tech/social media companies and the government. These cyber jihad issues also impact public safety and national security.
As Apple fights this encryption battle, with the backing of every major tech and social media company, what is missing is a unified statement from them declaring that they oppose terrorist use of their platform, and that they will work to come up with ideas to stop it, at the same time as they protect both privacy and freedom of speech. These groups need to come together to create industry standards for how tech companies and social media should deal with cyber jihad.
Aside from the iPhone in question in the San Bernardino shooting case, there are thousands of other iPhones and other Apple devices in the hands of many more jihadis, and jihadi organizations are closely following the current case. The more secure iPhones, Apple products, and other companies' products end up being, the more heavily jihadis will continue to rely on them, and the problem will not go away. The following report will give examples of how jihadis are using Apple products and how they are discussing and praising them on social media.
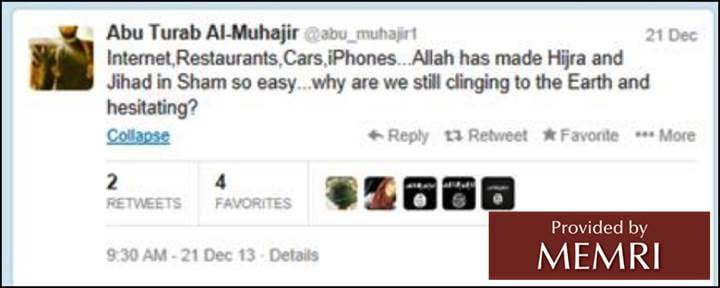
2013: Jihadi In Syria Touts iPhones As Helpful In Joining ISIS
A jihadi who traveled to Syria, Abu Turab Al Muhajir, who stated on his Twitter account that he is 25, from Chicago (or possibly Canada), and had joined the Islamic State of Iraq and Syria (ISIS), tweeted praise of his iPhone in his first tweet from Syria. On December 21, 2013, he tweeted: "Internet, Restaurants, Cars, iPhones... Allah has made Hijra and Jihad in Sham [Syria] so easy... why are we still clinging to the Earth and hesitating?"[2]
2014: Well-Known Jihadi In Syria Tweets Photo Of Handgun And iPad Mini, Noting "That's Jihad"
One example of how jihadis highlight their use of Apple products is a tweet by "Life of Mujahid," also known as Abu Bakr,featuring a handgun in an iPad Mini box, that was posted in 2014. Life of Mujahid's Twitter avatar features children playing and states "Jihad Is Our Playground."

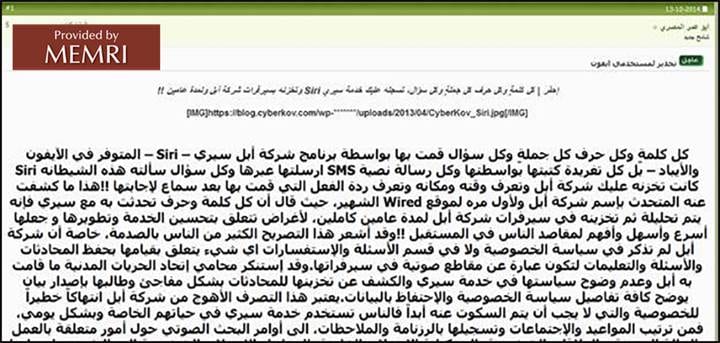
October 2014: Warning Against Using Search Via iPhone Personal Assistant Siri Posted On Leading Pro-ISIS Jihadi Forum
On October 13, 2014, a jihadi posted a warning on the leading pro-ISIS jihadi forum Shumoukh Al-Islam about using the search function of Siri, the Apple voice-controlled personal assistant for iPhone, iPad, and iPod Touch, and noting that search queries are saved on Apple servers for two years.
December 2014: ISIS Bans Use Of Electronic Devices With GPS, Calls Apple Products Particularly "Dangerous"
On December 13, 2014, ISIS issued an order banning its fighters from using "any electronic device or communication methods" with GPS services. The ban came in light of coalition airstrikes against ISIS's soldiers; ISIS stated that the devices' GPS capabilities were being used to pinpoint fighter locations. Because of the growing popularity of Apple products, ISIS also explicitly banned all of them - including phones and tablets - calling them "dangerous," and gave its fighters a one-month deadline to comply. After that, it said, any Apple devices would be confiscated and their owners would be investigated.[3] It should be noted that Apple was the only manufacturer that was specifically pointed out.
 Fatwa by ISIS-supporting imams discouraging the use of Apple products
Fatwa by ISIS-supporting imams discouraging the use of Apple products
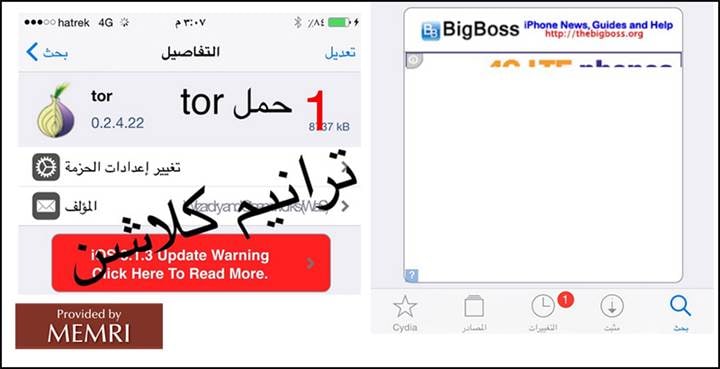
May 2015: Tutorial On Encrypting iPhones Posted On Leading Pro-ISIS Jihadi Forum
On May 28, 2015, a tutorial on encrypting iPhones was posted on the leading pro-ISIS jihadi forum Shumoukh Al-Islam. The tutorial was disseminated via the content-sharing website Justpaste.it, which is widely used by jihadis.
January 2016: ISIS Cyber Activist Tweets To Followers How To Use Apple iPod Touch For Secure Messaging
Tech-savvy jihad supporters frequently circulate information on Twitter about how to "secure" their phones against law enforcement surveillance. For example, on January 4, 2016, the well-known pro-ISIS cyber activist Abu Naseeha, who frequently provides cyber security tips, tweeted to his ISIS followers information on how to use an iPod Touch for secure messaging.
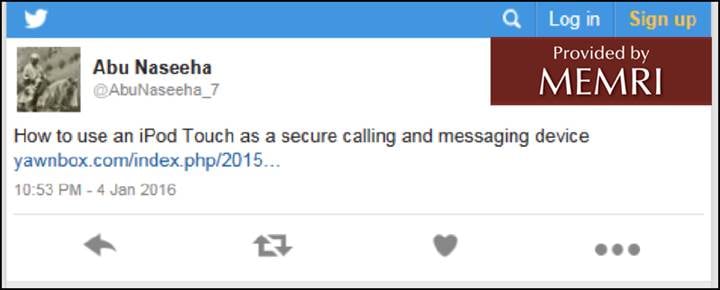
Abu Naseeha frequently disseminates links to open-source content that he thinks will be valuable to jihadis operating online. For example, he shared a September 2015 article on "How to use an iPod Touch as a secure calling and messaging device."[4]

The article that Abu Naseeha shared noted: "Modern communication technologies are abundant, but legacy phone calling and texting (SMS, MMS) are inherently insecure" and that "communications content in addition to metadata is collected and stored by various organizations and for many years." It added that "The modern iPod fills a much needed space. WiFi only. Generations 5 and 6 support iOS 8 which is the minimum requirement for Open Whisper System's free and open source Signal application."
Setting out the "advantages" of using Apple products, the article that Abu Naseeha shared stated:
- "Network: the iPod does not have inherent baseband insecurities or SIM card insecurities.
- "Network: you can control which WiFi networks to expose your device to.
- "Data at rest: The iPod employs default device encryption.
- "Data at rest: Signal employs default message database encryption and isolation.
- "Data in motion: Signal only uses modern protocols and state-of-the-art encryption.
- "OS security: Apple pushes security patches relatively quickly and the iPod is a more challenging device to infect with malware when used correctly.
- "Verifiability: Signal allows users to compare and verify encryption key fingerprints.
- "Verifiability: Signal is a free and open source software project that is publicly audited.
- "Scalability: other people with an iPod, iPhone or Android can freely install and use Signal.
- "Liability: when employed in a work place with supportive policy, work-oriented communications are compartmentalized from personal devices."
After naming a handful of disadvantages, the article that Abu Naseeha shared then provides "operational security practices": "Define a strict use case for your iPod for when certain groups of people ask. If you routinely travel, possibly through airport or border security, you don't want to raise suspicion of your device. It is an iPod after all, people will have expectations that it is for listening to music. You may be coerced to provide access to the device to prove its legitimacy. Plan ahead.
- "If your iPod is for professional services (like law, journalism, etc) only certain groups of people, maybe clients, should be aware of your communications practices. Your organization may even make certain policy decisions like making it public information that you can be reached via Signal for secure communications.
- "If your iPod is for personal use, since you can't risk connecting the iPod to computer systems to sync files, perhaps use it for photography and picture viewing."
February 2016: Jihadi Forum Member Asks About iPhone Safety
In light of Apple's refusal to cooperate with the FBI in unlocking the San Bernardino shooter's iPhone, one member of the major pro-Al-Qaeda jihadi forum Al-Fida' asked, in late February 2016, whether this means iPhones are safe to use.
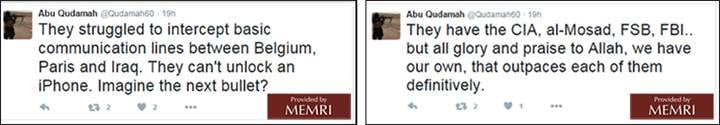
March 2016: ISIS Fighter Praises iPhone Security
In a March 2, 2015 tweet, an ISIS fighter touted jihadi superiority over American, Russian, and Israeli security services, noting how the FBI cannot unlock an iPhone.
March 2016: Instructions For Creating Twitter Account For iPhone Without A Phone Number Posted On Leading Pro-ISIS Jihadi Forum
On March 10, 2016, Aafaq Electronic Foundation posted, on the pro-ISIS jihadi forum Shumoukh Al-Islam, instructions for creating a Twitter account for an iPhone without providing a phone number.
March 2016: In Video, Pro-ISIS Hacking Group Shows How It Uses Video-Editing Software For Apple iPad, Reiterates Its Oath Of Fealty To ISIS Leader
On March 14, 2016, the pro-ISIS hacking group Cyber Caliphate Army disseminated, via its Telegram channel, a video showing members of the group editing video using "Cute Cut" editing software for the Apple iPad. The video (view it here) also featured the group reiterating its oath of fealty to ISIS leader Abu Bakr Al-Baghdadi.[5]

Pro-ISIS Elements On Popular Encrypted Communications App Telegram Discuss Using Apple Products For Encryption And Other Purposes
Another issue for Apple is the use of its products in conjunction with the popular encrypted communications app Telegram, the Berlin-based secure messaging app. Telegram's Channels Service, launched in late September 2015, allows individual message content to be transmitted to an unlimited number of subscribed users. ISIS has already created a number of channels on Telegram for sharing their content with thousands of followers. The app and its channels service are increasingly popular among jihadi supporters as well.
Although Telegram is Germany-based, it is available only via Apple's iTunes and Google's Google Play - both of which are U.S.-based. Thus, Apple, and for that matter Google, are stakeholders in Telegram, and are in a powerful position to pressure it to take action against ISIS's widespread use of its services.
Downloading Telegram from Apple's iTunes
The Telegram app allows anyone - including ISIS, Al-Qaeda, and other jihadi organizations and their supporters - to open a private channel for secret communications. Any smartphone owner can ask to join channels.[6] The following are just a few examples to highlight how jihadis are referring to the benefits of Apple.
The popular IPHONE Izizx Android channel on Telegram, while not a jihadi account, has many jihadi members who post to it, use content from it, and reference it. The channel, displayed below, has 18,333 members as of March 8, 2016.

In this post, IPHONE Izizx Android explains how to use Telegram and how to get it from iTunes.
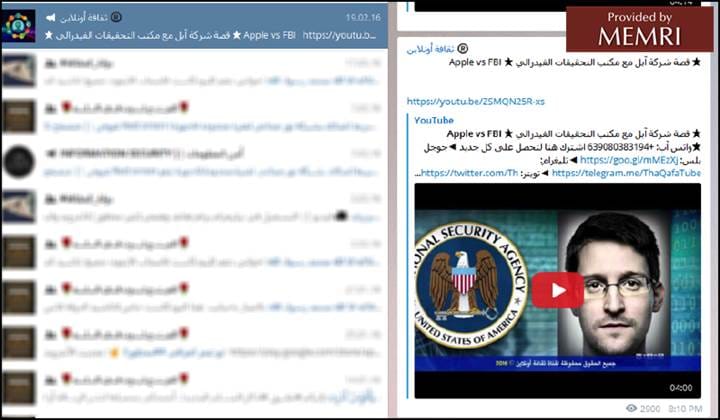
A post in the "Culture Online" group mentions the "Apple vs. FBI" fight; the video is a media report also on "Apple vs FBI":
The "Tarjamat" ("Translations") group also highlighted "Apple vs. FBI":
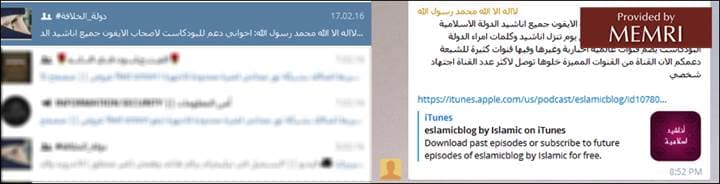
In the following group, "#Caliphate_State," information was shared about downloading from iTunes "eslamicblog by Islamic," with an explanation that it includes ISIS nasheeds and speeches by ISIS leaders that are released on it daily. The member sharing it asked other members with iPhones to support it:
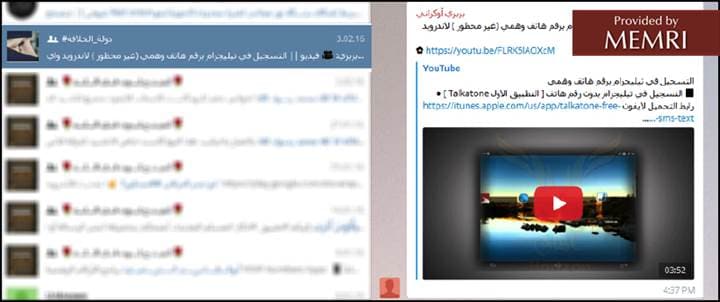
In the same group, jihadis discuss using the Talkatone app, which offers free calling and texting, including photos, and a free local U.S. phone number, and how to download it via iTunes:
Also in the "#Caliphate_State" group, Betternet, "the best proxy VPN for Wifi Hotspot Security," is promoted:

Betternet, a "free VPN for iPhones, iPad, and iPod Touch," on iTunes:

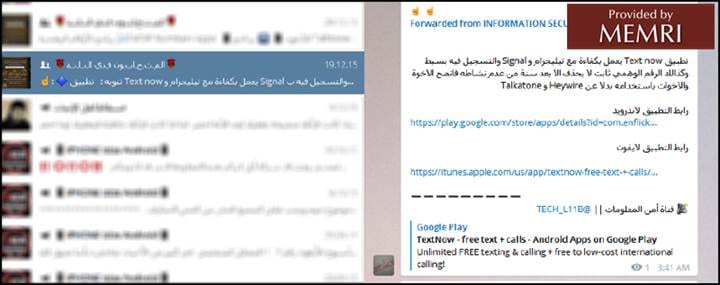
This discussion below in the "Al-Mutahaboun Fi-llah" group, focuses on communications apps, including Talkatone, and downloading them via iTunes:
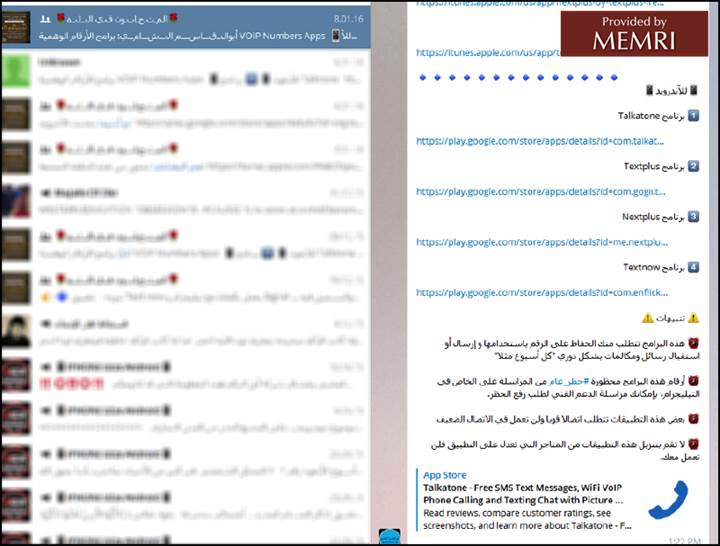
Below, information is shared in the "Al-Mutahaboun Fi-llah" group for using iTunes to download a messaging app:
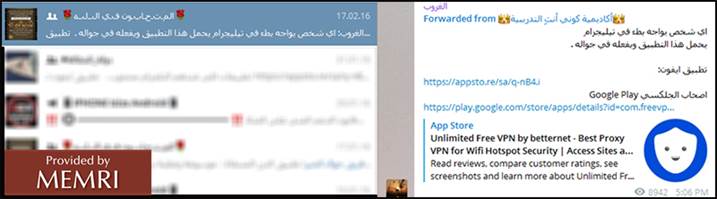
Betternet is promoted in the "Al-Mutahaboun Fi-llah" group:
An account with an avatar of Islamic State of Iraq leader Abu Mus'ab Al-Zarqawi in discussion about downloading encrypted messaging apps from iTunes, in which the Telegram channel "Unknown," which shares links for ISIS supporters to download encrypted messaging apps from iTunes and Google Play, provides one such link:
Sharing links to apps in iTunes in the "Unknown" group:
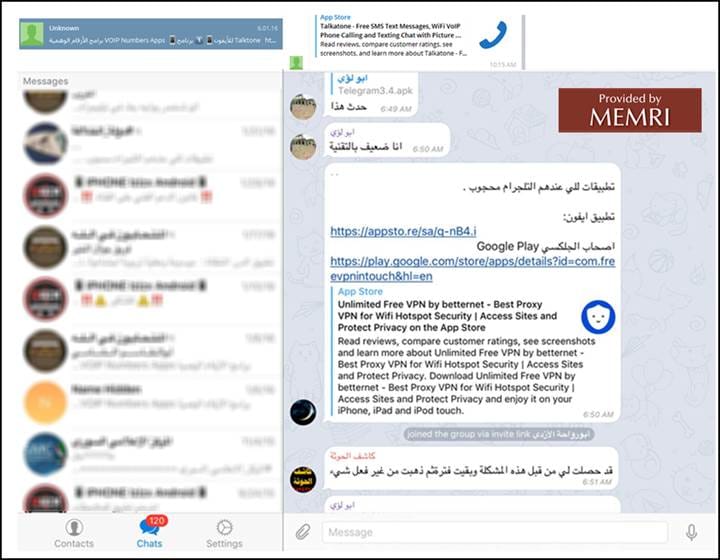
Below, a user in "Unknown" shares links to Betternet; the description here states that allows users to "Access Sites and Protect Privacy and enjoy it on your iPhone, iPad, and iPod touch."

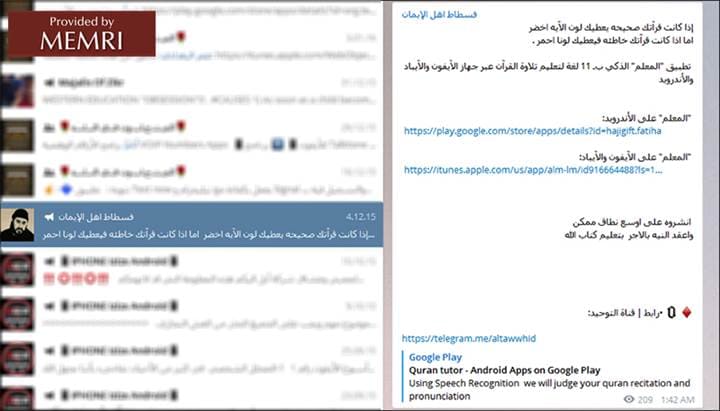
Telegram user "Fustat Ahl al-Iman" shares links to a "Quran Tutor" app using speech recognition software, available on iTunes, that is being used by ISIS sympathizers:
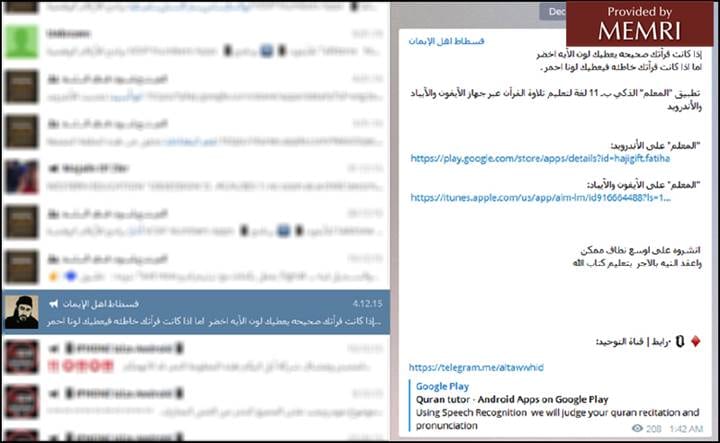
Another example of pro-ISIS elements focusing on Apple on Telegram was a discussion about Apple encryption on a pro-ISIS group called "Group for Chatting," whose avatar is a handgun. Participants discussed the use of VPNs on Apple products to evade detection by law enforcement and intelligence agencies. Participants asked about "vpn for apple," "ipad iphon," and "which one is recommended for apple." Other participants answered with the "best vpn for apple is Betternet" and "VPN HMA! Pro is a good one for Apple."


In other conversations, jihadis in various Telegram discuss the availability of apps in iTunes, showing how easy it is for anyone wishing to carry out a terror attack to obtain resources from Apple. Below, Telegram user Abu Aseed Al-Maqdisi shares tips for fellow ISIS supporters to download Telegram from iTunes:
Al-Qaeda's Global Islamic Media Front (GIMF) Channel On Telegram Discusses Using Apple Products
The Global Islamic Media Front (GIMF), an Al-Qaeda-affiliated media company, has been using Telegram since December 2015, for sharing updates and news-related items with its followers, on variety of cybersecurity topics.
The Telegram channel belongs to the technical section of GIMF, which since 2007 has been behind the development of various secure communication programs.[7] The conversations below include a focus on "making the iPhone more secure," how Apple uses patches to fill vulnerabilities, and more.
"Apple releases OS X system update 10.11.3, El Capitan. #MediaFrontTechnicalSection"
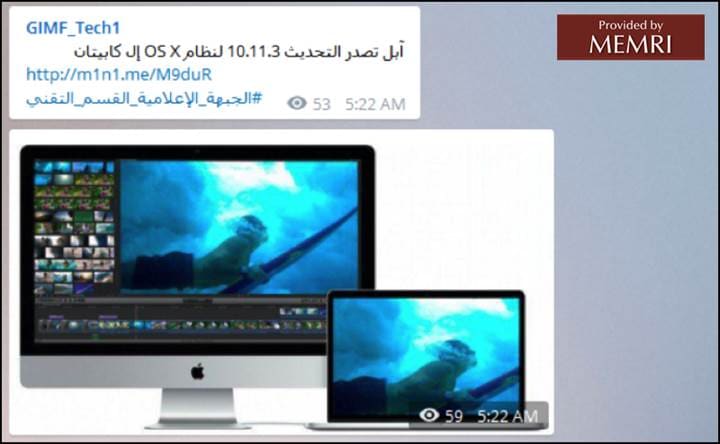
"10 tips to make the iPhone more secure. #MediaFrontTechnical Section"
 "Apple releases a patch for a vulnerability that allows stealing cookies files. #MediaFrontTechnicalSection"
"Apple releases a patch for a vulnerability that allows stealing cookies files. #MediaFrontTechnicalSection" 
"Information Security" Jihadi Tech Channel On Telegram Posts Links To Articles On Apple, Encryption
The "Information Security" channel on Telegram, with nearly 4,000 members, caters to jihadis' tech needs. It describes itself as "an independent technical channel publishing lessons and workshops in the field of electronic defense and information security, [and is] moderated by specialists in the field."[8]
On March 11, 2016, the Caliphate Cyber Army, a pro-ISIS jihadi hacking group, forwarded on its Telegram channel a post from Information Security about the Apple vs. FBI fight.

On March 9, 2016, Information Security shared links to articles in Arabic on Apple and on encryption issues:

*Steven Stalinsky is Executive Director of MEMRI; R. Sosnow is Head Editor at MEMRI.
Endnotes:
[1] Also demanding that Apple cooperate with the government's demands are family members of the victims. For example, Mark. M. Sandefur, father of one of the victims, wrote in an open letter to Apple CEO Tim Cook: "Recovery of information from the iPhone in question may not lead to anything new. But, what if there is evidence pointing to a third shooter? What if it leads to an unknown terrorist cell? What if others are attacked, and you and I did nothing to prevent it?... I urge you to consider the requested cooperation as your patriotic duty."
[2] MEMRI Cyber Jihad Lab report American ISIS Member From Chicago Active On Twitter And Facebook: 'Internet, Restaurants, Cars, iPhones... Allah Has Made... Jihad In Sham [Syria] So Easy,' January 3, 2014.
[3] MEMRI JTTM report Islamic State (ISIS) Bans Use Of Electronic Devices With GPS, Says Apple Products Are Particularly 'Dangerous', December 22, 2014.
[4] Yawnbox.com, September 12, 2015.
[5] MEMRI Cyber Jihad Lab report Cyber Caliphate Army Video Made With 'Cute Cut' For Apple iPad Shows Group Editing Videos Using Same Software, March 14, 2016.
[6] Telegram Messenger on iTunes and on Google Play.
[7] MEMRI Cyber Jihad Lab report On Telegram, Global Islamic Media Front (GIMF) Shares Technical Advice For Aspiring Jihadis, February 24, 2016.
[8] See MEMRI JTTM report Jihadi 'Help Desk,' Tech Channels On Telegram And Twitter Offer Tech Support, Tutorials, Up-To-Date Cyber Security Info, February 8, 2016.
Latest Posts




