Introduction
The MEMRI Cyber Jihad Lab (CJL) has received an exclusive copy of a report released May 25, 2015 by the cyber-security organization Tenshi, "Assessing The Computer Network Operation (CNO) Capabilities of the Islamic Republic of Iran." The report includes an analysis of the cyber threats posed by Iran, including its use of academia as a hotbed for cultivating future hackers, as well as a review of the most prominent and active Iranian hacker groups. The following is the CJL's review of this report.
"Iran's Interest In Further Developing Its Asymmetric Warfare Potential Has Never Been More Vigorous"
The report first assesses the current state of the cyber threat posed by Iran, noting that "Iran's interest in further developing its asymmetric warfare potential has never been more vigorous" and that the country is currently trying to break out of its "catch-up mode" and attain parity in Network-Centric Warfare. Iran, it says, is already experienced with measures regarding censorship, surveillance, and control of Internet and other data networks, and the country's thriving academic community focuses on topics such as software development, cryptography, and the localization of English-language materials into Farsi, which is a "major driving force behind the technological rise of Iran's understanding" of various forms of cyber warfare.
According to the report, the Iranian government has long tolerated the existence of a civilian hacking infrastructure, in which private Iranian citizens engaged in cyber warfare and shared knowledge, software exploits, and code, and in effect created a "closely nurtured ecosystem" stemming from the regime's desire to build the nation's offensive cyber capabilities along with cultivating the patriotic notions of civilian heroism on the cyber front.
Academia As A Farm System For Cyber Warriors
The report sets out how the Iranian regime utilizes the academic infrastructure that it controls to create nurturing environments for the development of cyber warfare capabilities. Iran's main academic incubators for the next generation of cyber warriors, it says, include the Iranian Scientific Society of C4I, the Iranian Society of Cryptology (ISC) along with its Student Branches of Cryptology, and the Student Branch of Command, Control, Communications, Computers, and Intelligence (SBC4I). It states: "Using a well proven methodology of solicitation of academic 'know-how' through invite-only events, and close nurturing of established connections among the academic community," the regime cultivates "the next generation of cyber warriors." For example, the ISC hosts a yearly conference on Security and Cryptology (ISCISC) which deals with topics such cryptography, infosec, steganography, and attacks on cryptographic algorithms. The Iranian Scientific Society of C4I also holds conferences and workshops on a variety of cyber topics.
Iranian Hacker Groups
Ashiyane Digital Security Team
The Ashiyane Digital Security Team is, according to the report, Iran's main hacker group, capable of conducting cyber-attacks against foreign adversaries, including the U.S. The group has already compromised thousands of servers around the world in order to spread Iranian propaganda, and utilizes hundreds of novice members to strengthen its position. Members of the Ashiyane Digital Security Team have appeared on Iranian TV and have hosted and participated in local conferences. They successfully train hundreds of new members on the basics of offensive cyber-capabilities (the group publishes an e-zine targeting novice users to become potential group members) and closely cooperate with the regime.

Ashiyane Digital Security Team leaders Behrooz Kamalian (Behrooz_Ice) and Nima Salehi (Q7X) on Iranian TV
SUPPORT OUR WORK

Iranhack Security Team
Another prominent hacker group, the Iranhack Security Team, is known, according to the report, for its tens of thousands of successful attacks. Some of its prominent members are known to have actively participated in other noted Iranian hacker groups, which helps create cross-pollination of technical know-how and knowledge bases. The group is known to have created custom client-side exploits for web-based services as well as offensive hacking software.

Members of Iranhack Security Team at a 2012 exhibition event
Iranian Datacoders Security Team

The Iranian Datacoders Security Team includes members from the Iranhack Security Team, according to the report, and also releases custom vulnerability exploits targeting web-based platforms.
Iran Security Team (SEPANTA Team)
The Iran Security Team (SEPANTA Team) engages in the creation of custom exploits for web-based clients, according to the report. Several of its members are also members of another hacker group, the IDH Security Team.
IDH Security Team
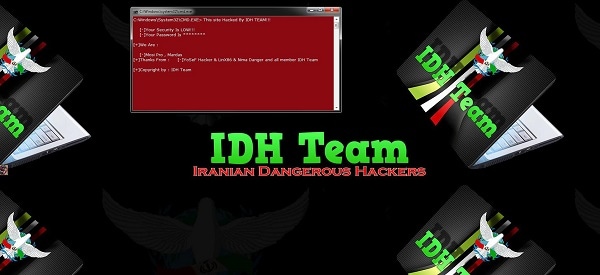
The IDH Security team is known, according to the report, to have actively defaced hundreds of websites and possessing various offensive cyber capabilities.
NOPO Digital Security Team

The NOPO Digital Security Team engages in versatile cyber-attacks and website defacements, according to the report. It includes members also tied to Iranhack Security Team.
Other Hacker Groups
Other hacker groups mentioned in the report are Bastan Security Team, Shekaf Security Team, Mafia Hacking Team, Iran Black Hats Team, DiaGram (Advisor Security Team), Delta Hacking Security Team, Digital Boys Underground Team, and IrIst Security Team.
Conclusion
"Assessing The Computer Network Operation (CNO) Capabilities Of The Islamic Republic Of Iran" concludes with a summary of its main thrust - that Iran is actively developing its offensive cyber capabilities by creating academic incubators for future cyber warriors, and by nurturing and often collaborating with civilian hacker groups who themselves cross-pollinate members, knowledge, and tools so as to create an extensive and decentralized ecosystem of cyber knowledge and ability.
Read The Full Report
Readers who wish to read the full report may write to Tenshi, [email protected] to purchase it.




