On August 27, 2016, the Twitter account of Ghost Squad Hackers (GSH) claimed credit for hacking the websites of the Bank of Israel and the Israeli Prime Minister's Office. The group used a denial-of-service (DoS) vulnerability in the underlying web servers to take down the websites. S1ege, GSH's leader, told Softpedia that the Bank of Israel website was back online after six hours, after the bank's IT staff moved the site to new servers.[1]
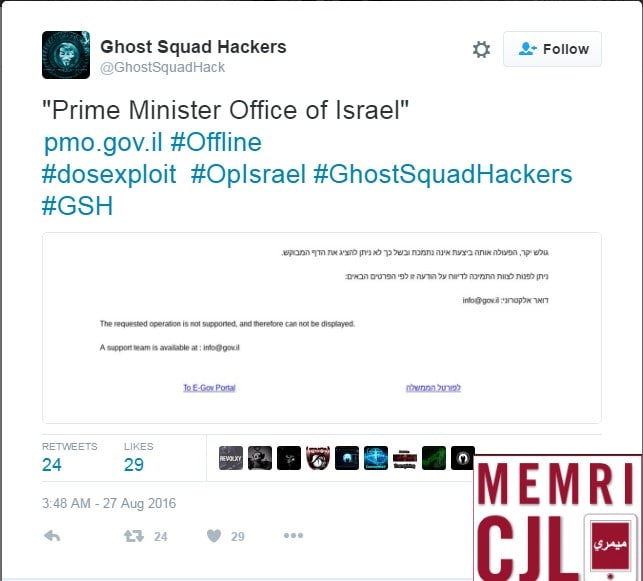 Post on GSH's Twitter feed claiming credit for hack of the Israeli Prime Minister's Office on August 27, 2016
Post on GSH's Twitter feed claiming credit for hack of the Israeli Prime Minister's Office on August 27, 2016
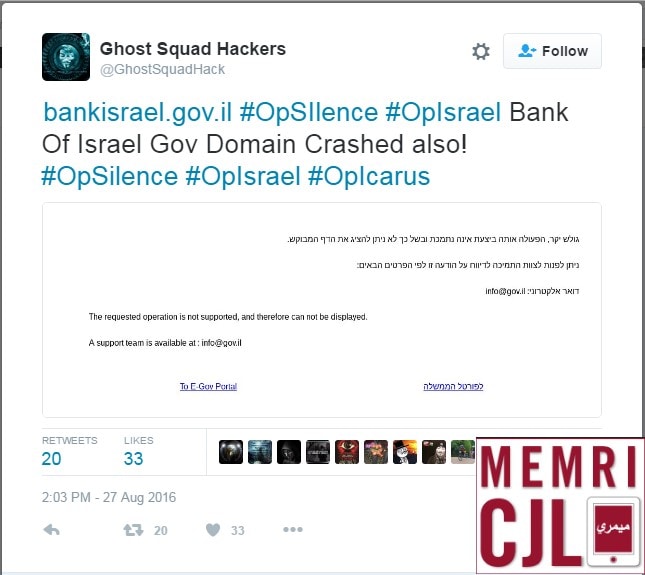 Post on GSH's Twitter feed claiming credit for the hack of the Bank of Israel, August 27, 2016
Videos Of Ghost Squad Hackers Claiming Credit For Hacks
Post on GSH's Twitter feed claiming credit for the hack of the Bank of Israel, August 27, 2016
Videos Of Ghost Squad Hackers Claiming Credit For Hacks
The following videos claiming responsibility for the hacks were shared with Softpedia by S1ege. Both videos feature a claim of responsibility and a warning to Israel generated by a text-to-speech application.
To watch the first video, please click here. Bank of Israel Crashed by Ghost Squad Hackers from MEMRI - CJL on Vimeo.Asked for the reason behind the hack, S1ege, GSH's leader, told Softpedia the following:
"We are attacking Israel for the ongoing atrocities they are committing on the Palestinian people. They just recently bombed Gaza again. The genocide needs to end. They are expanding an empire into land/ground that they do not own, over a book. There is a perpetual silence in the mainstream media. We hope our attacks will bring more awareness to this subject and bring more protests to this issue."
S1ege also spoke of plans for future attacks to come in the following days:"Yes we have some attacks planned for Israel. We, in [the] past, leaked IDF [Israel Defense Force]'s database. We plan to do similar attacks in the future if there is no word of the ongoing genocide in Israel. The United States mainstream media works as stenographers for the U.S. government and speaks nothing of this its corruption at it's [sic] finest. We will not stand idly by and let it continue. We also plan to attack the Syrian government."[2]
Background On Ghost Squad HackersIn early June, GSH announced #OpSilence, which they characterized as months-long DDoS attacks against mainstream media outlets due to their perceived failure to report on conflict in Palestine and war crimes happening in Syria. Outlets targeted in #OpSilence included FOX News and CNN. GSH also claimed to be behind #OpIcarus, a month-long DDoS campaign against banks and other financial institutions around the world.
On July 31, 2016, GSH hacked the Twitter account of Afghan Chief Executive Abdullah Abdullah.[3]
On August 23, 2016, GSH also claimed on its Twitter account to have hacked the Israeli Ministry of Foreign Affairs.[4]
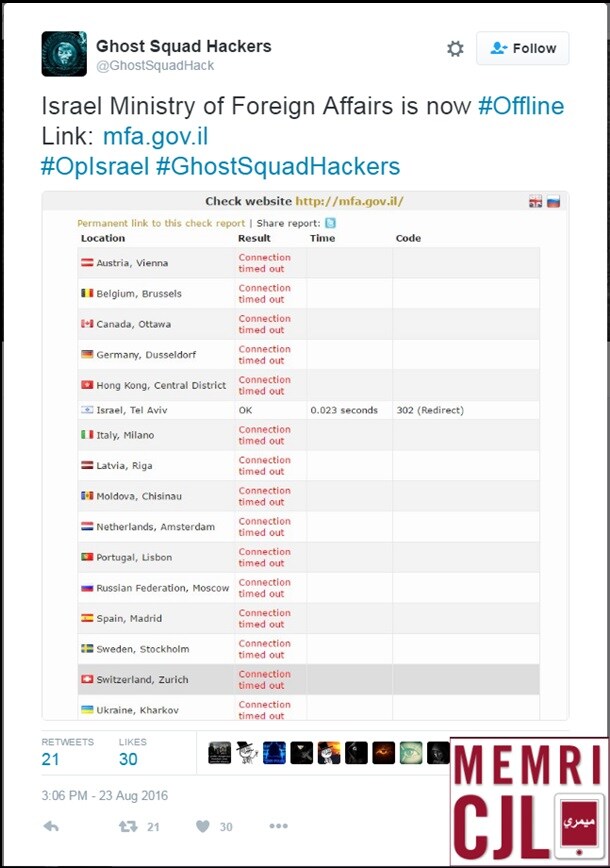 Twitter post claiming credit for hacking the Israeli Foreign Ministry
Twitter post claiming credit for hacking the Israeli Foreign Ministry
GSH was also responsible for revealing personal details of members of the United Cyber Caliphate (UCC), including its leader, Mauritania Attacker. In the wake of this "dox," S1ege told AnonHQ.com of the group's affiliation: "Although we are Muslims Christians and Atheist we have no one religion and we accept all. But (it's true that) majority of us are Muslims and we believe in true Islam not this fake ISIS shit." [5]
Social Media PresenceGSH and its leader, S1ege, continue to be active on Facebook and Twitter. Below is a review of related social media accounts.
FacebookGSH's Facebook page was created April 8, 2015. As of August 30, 2016, the page has 23,937 likes.
 Official GSH Facebook Page
S1ege's Facebook page was created February 2, 2016.
Official GSH Facebook Page
S1ege's Facebook page was created February 2, 2016.
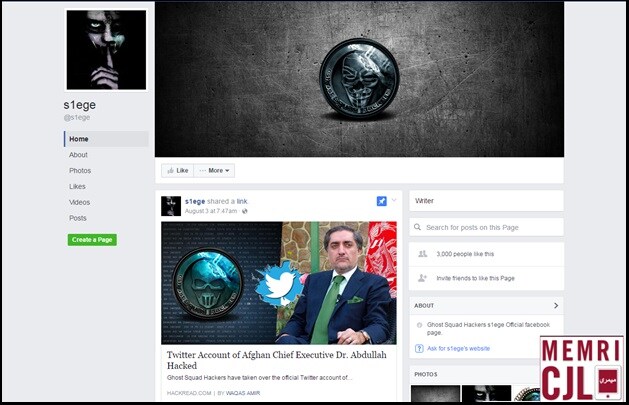 Facebook page of GSH leader s1ege.
Twitter
Facebook page of GSH leader s1ege.
Twitter
The official Twitter page of GSH, created January 26, 2016, has 303 tweets and 3,289 followers as of August 30, 2016.
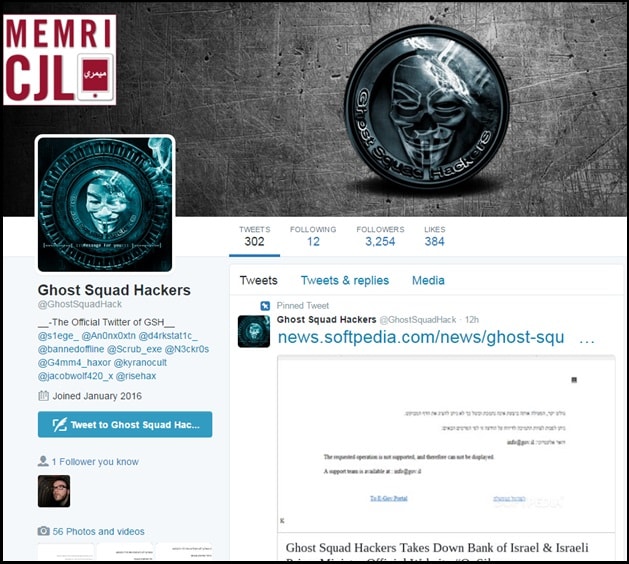 Official GSH Twitter Page
Official GSH Twitter Page
As of August 30, 2016, S1ege's Twitter page, created May 12, 2016, has 599 tweets and 1,818 followers.
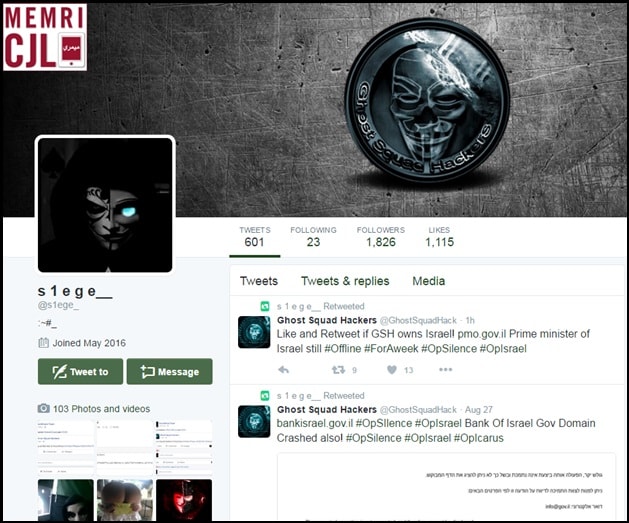 Twitter page of s1ege
Twitter page of s1ege
 S1ege wearing a decorated Guy Fawkes mask.
Endnotes:
[1] News.softpedia.com, August 28, 2016.
[2] News.softpedia.com, August 28, 2016.
S1ege wearing a decorated Guy Fawkes mask.
Endnotes:
[1] News.softpedia.com, August 28, 2016.
[2] News.softpedia.com, August 28, 2016.
[3] See MEMRI CJL, Ghost Squad Hacks Twitter Account of Afghan Chief Executive, August 2, 2016.
[4] Twitter.com/GhostSquadHack, August 23, 2016.[5] For more information on the UCC dox, see MEMRI CJL Identity Of Main Pro-ISIS Hacking Group United Cyber Caliphate Members Revealed, July 26, 2016.
Latest Posts



