Table Of Contents
Government Officials Warn Of Jihadi Use Of Encryption; U.S. Tech Giants Add Encryption Technology Expected To Be Heavily Used By Jihadis Due To Snowden Revelations
Al-Qaeda In The Indian Subcontinent (AQIS) Uses Encryption In First Issue Of Its English-Language Magazine Resurgence
Al-Qaeda In The Arabian Peninsula (AQAP) Inspire Magazine Issue 13 - Magazine Known For Using Encryption Technology; Second Edition In A Row To Have Suspended Email Address For Security Reasons - Utilizes Encryption
GIMF Releases Updated Version Of Android Secure Communication App, Refers To The 'Cooperation Of Global [Communication] Companies With The International Intelligence Agencies' As Reason Behind Update
Al-Fajr Technical Committee Releases Android App For Secure Communication, Announces New Website
Islamic State (ISIS) And Encryption
Islamic State Releases Third Issue Of Its English-Language Magazine Dabiq, First Time It Releases Encryption Technology
Pro-Islamic State (ISIS) Twitter Account Provides Guidelines For Using Tor, Encrypted Communication
Islamic State (ISIS) Bans Use Of Electronic Devices With GPS, Says Apple Products Are Particularly 'Dangerous'
ISIS-Affiliated Twitter Account Tells Mujahideen: Insulate Your Mobile Phones So Spy Planes Can't Pinpoint Your Location
ISIS-Affiliated Forum Posts French-Language Guide To Help French Speakers Join The Forum And Write On It Using Tor
Shumoukh Al-Islam Forum Opens Doors For Jihadis Including ISIS And Al-Qaeda Affiliate In Syria Jabhat al-Nusra, To Submit Questions To Fighting Jihadi Groups In Syria, Provides Public Key For Secure Communication Via Asrar Al- Mujahideen Program
Pro-ISIS Jihadi Forum Warns Members Against Using Private Messages On Forum, Recommends Using Asrar Al-Mujahideen Program For Secure Communication
Pro-ISIS Jihadis Offer Tutorials On Obtaining Fake U.S. Phone Numbers To Maintain Access To Social Media, Circumvent Censorship
Jihadis Circulate Tutorials On Maintaining Online Anonymity And Security, Suggest Ways To "Hide From The Crusader Alliance"
Jihadis Discuss "Ways Of Hiding From The Crusader Alliance"
Jihadi Warns Against Enemy Use Of Metadata, Offers Ways To Remove It
Ask.fm: Gateway To More Secure Jihadi Chat; As Kik, ChatSecure Grow In Popularity, Jihadis Become Wary Of These And Other Encryption Services
SureSpot - Latest App Used By Online Jihadis, Including The Infamous ShamiWitness
On Twitter, Jihadis Discuss Benefits Of Using SureSpot
Appendix: Mysterious Online "Global Islamic Intelligence Media" (GII) Releases Video Via Twitter And Youtube Detailing Phone Tracking Technology, Advises Jihadis On Ways To Avoid Detection And 'Spies'; "Every Mujahid That Does Not Take The Right Precautions [Online] Can Be A Tool In The Hand Of The Enemy"
Government Officials Warn Of Jihadi Use Of Encryption; U.S. Tech Giants Add Encryption Technology Expected To Be Heavily Used By Jihadis Due To Snowden Revelations
On January 16, 2014, at a joint press conference with British Prime Minister David Cameron, President Obama said, when asked about methods used by terrorists to avoid intelligence collection: "[W]ith respect to the issue of intelligence-gathering, signal intelligence, encryptions, this is a challenge that we have been working on since I've been President... Social media and the Internet is the primary way in which these terrorism organizations are communicating... when we have the ability to track that in a way that is legal, conforms with due process, rule of law, and presents oversight, then that's the capability that we have to preserve... we're working with partners like Great Britain and the United Kingdom, but we're also going to be in dialogue with the companies to try to make that work."[1]
As research from the MEMRI Jihad & Terrorism Threat Monitor has extensively documented, since January 2007 Al-Qaeda has been using encryption tools for its online activities, particularly for communication efforts, often utilizing security software based on military grade technology.[2]Their goal has been to hide messages and to protect data transferred via networks, the Internet, mobile phones, e-commerce, Bluetooth, and the like. This development was in direct response to various security breaches of its websites over the years by Western government agencies.
Following the killing of Osama bin Laden, more information on the extent of Al-Qaeda's use of encryption became known, as it was revealed that much of the material seized at bin Laden's compound was encrypted and stored electronically on computers, laptops, hard drives, and storage devices. Previously, Nasir Al-Wuheishi, thought to be deputy to Al-Qaeda leader Ayman Al-Zawahiri, known to have been bin Laden's secretary, and currently a top Al-Qaeda in the Arabian Peninsula (AQAP) leader, discussed the organization's use of encryption software and its use for talking to recruits, planning attacks, and other strategic purposes:[3] "For our part, we will make contact with anyone who wants to wage jihad with us, and we will guide him to a suitable means to kill the collaborators and the archons of unbelief - even in his bedroom or workplace. Anyone who wants to give support to [Al-Qaeda in the Arabian Peninsula's] operational side and to give tithes [to the organization] can contact us through a special email [set up] for this purpose, using the 'Mujahideen Secrets' software and employing the proper security measures..."[4]
Numerous current and former U.S. and Western government officials have discussed the issue of Al-Qaeda's and other terrorist groups' growing reliance on encryption technology. On September 10, 2014, Nicholas Rasmussen, who is now director of the National Counterterrorism Center, said at a September 10, 2014 Senate hearing titled "Cybersecurity, Terrorism, and Beyond: Addressing Evolving Threats to the Homeland: "Al-Qaeda's core is increasingly encouraging groups and individuals to act independently in support of the global movement. With no longer holding an expectation that regional affiliates will discuss or clear their operations plans with Al-Qaeda senior leadership prior to execution. And this evolution is the result of an adaptive enemy... Our counterterrorism operations continue to degrade Al-Qaeda's core ability to lead the global terrorist movement and to plan sophisticated attacks from its place in the FATA [Federally Administered Tribal Areas of Pakistan]. But as a result of leaks and disclosures, including those attributable to Edward Snowden, terrorists now understand the scope and scale of Western collection capabilities, and they're changing the way they communicate. They're adopting encryption technologies. They're shifting accounts, or avoiding altogether the use of electronic communications, all of which frustrate our counterterrorism effortsIn short, we cannot connect the dots... if we can't collect the dots that matter the most. And our collection is challenged in this new environment."
Former National Counter Terrorism Center director Matthew Olsen told CNN on October 21, 2014: "They've changed how they encrypt their communications and adopted more stringent encryption techniques. They've changed service providers and email addresses, and in some cases have dropped off altogether. They suspected we had this capability before the NSA stolen documents were made public. But is has become a really concerted effort by a number of these targets, people we were following, and it's made it harder for us to collect against them."[Q: Have we lost them as a result of that?] "Yes. We've lost a collection against some individuals. People that we were concerned about. We are no longer collecting their communications. So we lost insight into what they were doing... People we were concerned about."
Robert Hannigan, the director of the UK Government Communications Headquarters (GCHQ), wrote on November 3, 2014 in the Financial Times: "The ISIS leadership understands the power this gives them with a new generation ... capitalizing on Western freedom of expression ... for encrypting messages or making them anonymous which were once the preserve of the most sophisticated criminals or nation states now come as standard. These are supplemented by freely available programs and apps adding extra layers of security, many of them proudly advertising that they are 'Snowden approved.' There is no doubt that young foreign fighters have learnt and benefited from the leaks of the past two years. GCHQ and its sister agencies, MI5 and the Secret Intelligence Service, cannot tackle these challenges at scale without greater support from the private sector, including the largest US technology companies which dominate the web..."
While Al-Qaeda had been using encryption technology since 2007, the emphasis it has placed on such technology has markedly increased following media accounts of Edward Snowden's revelations of U.S government tapping into electronic communications of U.S. technology companies. In addition, jihadis have expressed hesitancy to use certain platforms and to communicate as openly as they had previously. This was especially true in the first six months following the disclosures; however, some groups, as this report will show, have now gone back to their previous methods.
Another recent development was highlighted by a report by Ellen Nakashima in the Washington Post, according to which the instant messaging platform WhatsApp, bought recently by Facebook and increasingly popular among jihadis, had begun encrypting all data by default. According to the article, "Open Whisper Systems... [has] partnered with WhatsApp to build in end-to-end encryption that will make it impossible for foreign governments and U.S. agencies to intercept text messages, even with a warrant." Apple and Google have also announced that the data on their mobile devices would be encrypted by default. While privacy advocates claim that this will help dissidents and human rights activists protect their communications against governments and hackers, law enforcement officials said that the encryption hinders legitimate investigation of suspects: "FBI Director James Comey said recently that the 'post-Snowden pendulum has swung too far,' referring to tech companies' reactions to the revelations of widespread government surveillance by former National Security Agency contractor Edward Snowden."[5]
In the wake of the Charlie Hebdo and subsequent attacks in Paris, British Prime Minister David Cameron said, on January 12, 2015, that he would consider banning encryption services, such as Snapchat and WhatsApp, if they did not allow his country's intelligence agencies access to sought communications. In view of this proposed strategy, Prime Minister Cameron urged President Barack Obama to pressure Facebook, Twitter and others to cooperate more with British intelligence agencies against extremism.[6]
Andrew Parker, the head of the UK's MI5, warned Apple and Google on January 8, 2015 that their efforts to keep its users' communications private was "closing off" his agency's ability to locate and apprehend terrorists. He went on to state, "Wherever we lose visibility of what they are saying to each other, so our ability to understand and mitigate the threat that they pose is reduced."[7]
L. Gordon Crovitz, former publisher of The Wall Street Journal, criticized U.S. social media companies on November 23, 2014 for their plans to add encryption: "Apple, Google, Facebook and others are playing with fire," he wrote, adding that their behavior "highlights the risks that Silicon Valley firms are taking with their reputations by making it impossible for intelligence agencies or law enforcement to gain access to these communications. In September, marketers from Apple bragged of changes to its operating system so that it will not comply with judicial orders in national-security or criminal investigations..."Unlike our competitors," Apple announced, "it's not technically feasible for us to respond to government warrants." This encryption was quickly matched by Google and the WhatsApp messaging service owned by Facebook."[8]
The Snowden revelations have had a direct impact on the way jihadis have been using the Internet and social media, and have even generated an extraordinary level of paranoia among them. For example, on December 13, 2014, ISIS issued an order banning all of its fighters from using devices equipped with GPS, particularly Apple devices, since those, it said, were particularly "dangerous." It should be expected that if and when companies, including Google, Android, WhatsApp, and Apple, add encryption technology, they will be heavily utilized by jihadi groups.
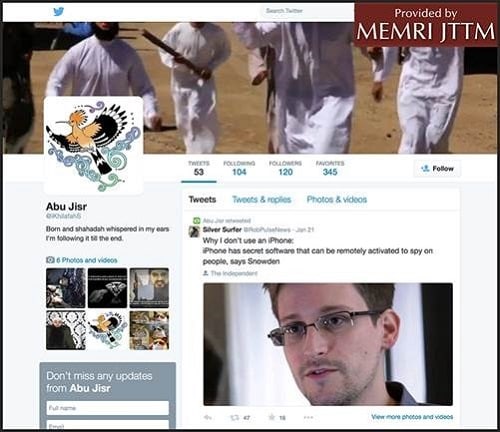
A recent example highlighting how jihadis are following developments related to the Snowden revelations is a January 21, 2015 retweet by Abu Jisr (@iKhilafaS) of an article in the Independent warning about iPhone's "secret software."
This report will explore developments in jihadi use of encryption over the last six months, since MEMRI's previous report on this subject.
See also:
*Al-Qaeda's Embrace of Encryption Technology - Part I: 2007-2011
*Al-Qaeda's Embrace Of Encryption Technology - Part II: 2011-2014, And The Impact Of Edward Snowden
The full text of this report is available to MEMRI Jihad and Terrorism Threat Monitor subscribers.
Subscription information is available at this link.
JTTM subscribers can visit this page to view the report.
Latest Posts



